A year ago, there seemed to be a glimmer of optimism in the ongoing battle of the cybersecurity industry against ransomware groups. It appeared that fewer corporate targets had succumbed to hackers’ demands for payment in 2022, and cybercriminals were experiencing reduced earnings from their malicious activities. The combination of enhanced security measures, heightened law enforcement attention, international sanctions against ransomware operators, and increased scrutiny of the cryptocurrency sector suggested a potential victory over the ransomware threat.
However, that brief respite now appears to have been merely a temporary interruption in the trajectory of ransomware’s ascent to becoming one of the most profitable and disruptive forms of cybercrime globally. In fact, 2023 proved to be its most devastating year yet.
No Reprieve from Ransomware
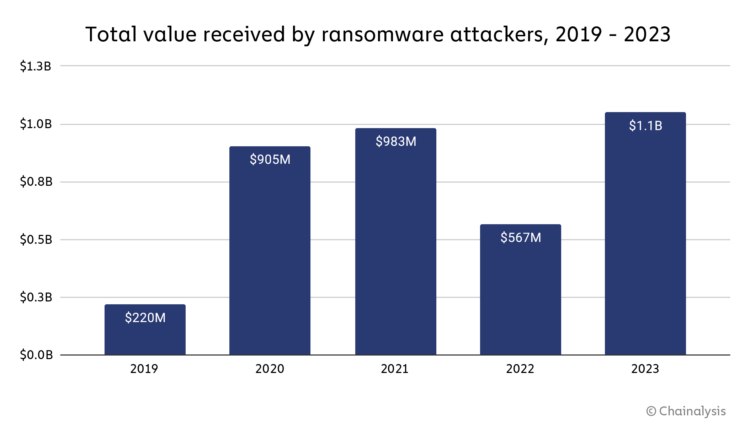
On last week, cryptocurrency tracking firm Chainalysis released new data from its annual crime report indicating that ransomware payments exceeded $1.1 billion in 2023, as tracked across blockchain transactions. This figure represents the highest amount Chainalysis has ever recorded for a single year, nearly doubling the total from the previous year. Indeed, the company now characterizes the relatively low $567 million in ransom payments for 2022 as an aberration, as the overall trend of extortion transactions has consistently increased since 2020, culminating in the current record-breaking figures. For Dallas – Fort Worth residents, 2023 also represents a troubling year, as city and county IT infrastructures have fallen to victim to cyberthreats in several occasions.
Jackie Burns Koven, head of threat intelligence at Chainalysis, remarks, “It’s as if we’ve resumed exactly where we left off, with the intense onslaught experienced during the Covid-19 pandemic in 2020 and 2021. It feels like all bets are off.”
The unprecedented $1 billion-plus in extortion payments in 2023 was driven, in part, by the sheer volume of ransomware attacks. According to cybersecurity firm Recorded Future, there were 4,399 ransomware attacks reported last year, based on news accounts and ransomware groups’ public disclosures of victims on their dark web platforms—an intimidation tactic frequently employed by these groups to coerce victims while threatening to release their compromised data. This represents a significant increase compared to the 2,581 total attacks in 2022 and 2,866 in 2021.
Fewer Victims Now Represent a Larger Share of the Payout
Despite this surge in attack volume, there appears to be a somewhat positive trend emerging: According to data from incident response firm Coveware, which often negotiates with ransomware groups on behalf of victims, only 29 percent of ransomware targets paid a ransom in the fourth quarter of 2023. This marks a substantial decline from payment rates of between 70 and 80 percent observed for most of 2019 and 2020.
Despite the decreasing number of victims who comply with ransom demands, the overall amount collected by ransomware groups continues to rise, fueled by an increasing number of cybercriminals entering the lucrative sector and executing more attacks. Allan Liska, a threat intelligence analyst at Recorded Future, suggests that the widespread publicity surrounding ransomware functions as a form of marketing, attracting additional opportunistic hackers akin to sharks drawn to the scent of blood in the water. “With all these ransomware attacks making headlines,” Liska explains, “criminals naturally gravitate towards the areas where they witness significant profits being generated.”
Random Demands Are Now Also Getting Larger
Chainalysis highlights that the unprecedented $1.1 billion in ransom payments made in 2023 was also propelled by ransomware attackers demanding larger sums from carefully selected victims. Many of these targets were chosen based on their vulnerability to withstand a crippling attack and their capacity to pay, a strategy referred to by Chainalysis’ Burns Koven as “big game hunting.” Consequently, nearly 75 percent of the total value of ransomware payments in 2023 came from transactions exceeding the $1 million threshold, compared to just 60 percent in 2021.
In hindsight, the dip in total ransom payments observed in 2022 appears to be an anomaly amidst the relentless evolution of ransomware tactics. Chainalysis and other security firms attribute this downturn to various factors, including the conflict in Ukraine, which disrupted Ukrainian ransomware operators and diverted the attention of Russian hackers toward political hacking endeavors, as well as international sanctions that discouraged victims from paying ransoms and significant law enforcement interventions.
For instance, the prolific ransomware group Conti disbanded following internal conflicts triggered by divergent opinions on Russia’s war in Ukraine, with one leader supporting the conflict and another leaking the group’s internal communications. Many former members of Conti then regrouped under the banner of the Hive ransomware operation, which was later revealed to have been infiltrated by law enforcement agencies, leading to the prevention of over $200 million in ransom payments. Burns Koven describes the dissolution of Conti as an almost perfect storm.
Conversely, the Cl0p ransomware group capitalized on a vulnerability in the MOVEit file transfer application to target thousands of victims, particularly medical companies and government agencies holding vast amounts of sensitive data. Cl0p amassed over $100 million from this mass exploitation, comprising a significant portion of ransom payments in June and July of 2023.
Despite the continued growth of the ransomware business, the crackdown on cryptocurrency crime by regulators and law enforcement has forced ransomware groups to seek new methods for laundering money and, in some cases, delay cashing out ransom payments for fear of seizure or freezing. Burns Koven suggests that faster reporting of ransom payments to law enforcement could further aid in tracing and preventing the liquidation of these funds.
While efforts to disrupt ransomware operations show promise, the persistent growth of ransomware activities suggests that additional measures are needed. Tightening regulations on money launderers, ransom-paying victims, and hackers themselves may be necessary to effectively address the problem.
Businesses Need To Protect Themselves From Ransomware
Protecting against ransomware requires a multi-layered approach to security. Here are some strategies that businesses can implement:
- Employee Training: Educate employees about phishing emails, suspicious websites, and the importance of not clicking on unknown links or downloading attachments from unknown sources.
- Regular Backups: Implement a regular backup strategy for all critical data. Ensure that backups are stored securely and are not directly accessible from the network to prevent them from being encrypted by ransomware.
- Update Software Regularly: Keep all software, including operating systems, antivirus programs, and applications, up to date with the latest security patches to protect against known vulnerabilities.
- Network Segmentation: Segment the network to restrict access to sensitive data. This limits the spread of ransomware in case of an infection.
- Use Strong Authentication: Implement strong authentication methods, such as multi-factor authentication (MFA), to prevent unauthorized access to systems and data.
- Access Controls: Limit user permissions to only what is necessary for their role. This reduces the likelihood of ransomware spreading across the network.
- Network Monitoring: Use intrusion detection systems (IDS) and intrusion prevention systems (IPS) to monitor network traffic for suspicious activity and potential ransomware attacks.
- Endpoint Protection: Deploy advanced endpoint protection solutions that can detect and block ransomware before it can execute on endpoints.
- Incident Response Plan: Develop and regularly test an incident response plan that outlines the steps to take in the event of a ransomware attack. This includes procedures for containing the infection, restoring data from backups, and communicating with stakeholders.
- Regular Security Audits: Conduct regular security audits and penetration testing to identify and address vulnerabilities before they can be exploited by attackers.
- Security Awareness Training: Continuously educate employees about the latest ransomware threats and tactics used by cybercriminals to improve their ability to recognize and respond to potential attacks.
By implementing these measures, businesses can significantly reduce their risk of falling victim to ransomware attacks and minimize the impact if an attack does occur. However, the list above represents only a small sample of an overall robust cybersecurity strategy that businesses owners are highly advised to implement. Partnering with a security focused IT company greatly increases your cyber readiness posture should the unthinkable happen.







