Early intervention allows you to be proactive in addressing network computer systems security.
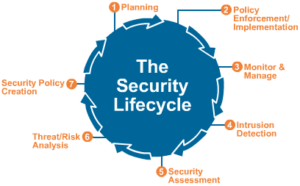
Network Security Audits/Assessment
LG Networks offers the benefit of security audits/assessments to identify vulnerabilities in your IT network before they are compromised. With the ever-growing increase in IT security breaches, this is now more important than ever. Our assessment can address these points of potential vulnerability:
![]()
- Application vulnerability
- Communication vulnerability
- Hardware/OS vulnerability
- Network Vulnerability
- Trusted sources and internal users
- Un-trusted sources
- User authentication/permissions vulnerability
- Viruses introduced via external means
Network Security Requirements
Best practice network security considerations should include:
- Centralized anti-virus
- Access controls
- Firewalls
- Smart cards
- Biometrics
- Intrusion detection
- Policy management
- Vulnerability scanning
- Physical security mechanisms
- Encryption
Learn More
For an assessment of your present security status and to learn what LG Networks can do to protect your business, click here to schedule a consultation or call us at 972-528-6546.


