
Cloud and Hosted IT Services: How to Spot the Difference
When discussing operational efficiency in business meetings where tech is part of their day-to-day operations, terms like “cloud computing” and “hosted IT services”

When discussing operational efficiency in business meetings where tech is part of their day-to-day operations, terms like “cloud computing” and “hosted IT services”

In today’s digital age, cybersecurity is a concern that affects businesses of all sizes. While large corporations often dominate the headlines when it

The looming threat of successful cyber attacks stands as one of the most pressing risks confronting organizations across all sectors and sizes. Both

We recognize the distinct hurdles that businesses in the Dallas – Fort Worth Area encounter in confronting cyber threats like ransomware. While we

Following a recent cyber assault on Omni Hotels & Resorts, leading to a temporary halt of its systems to safeguard and control its
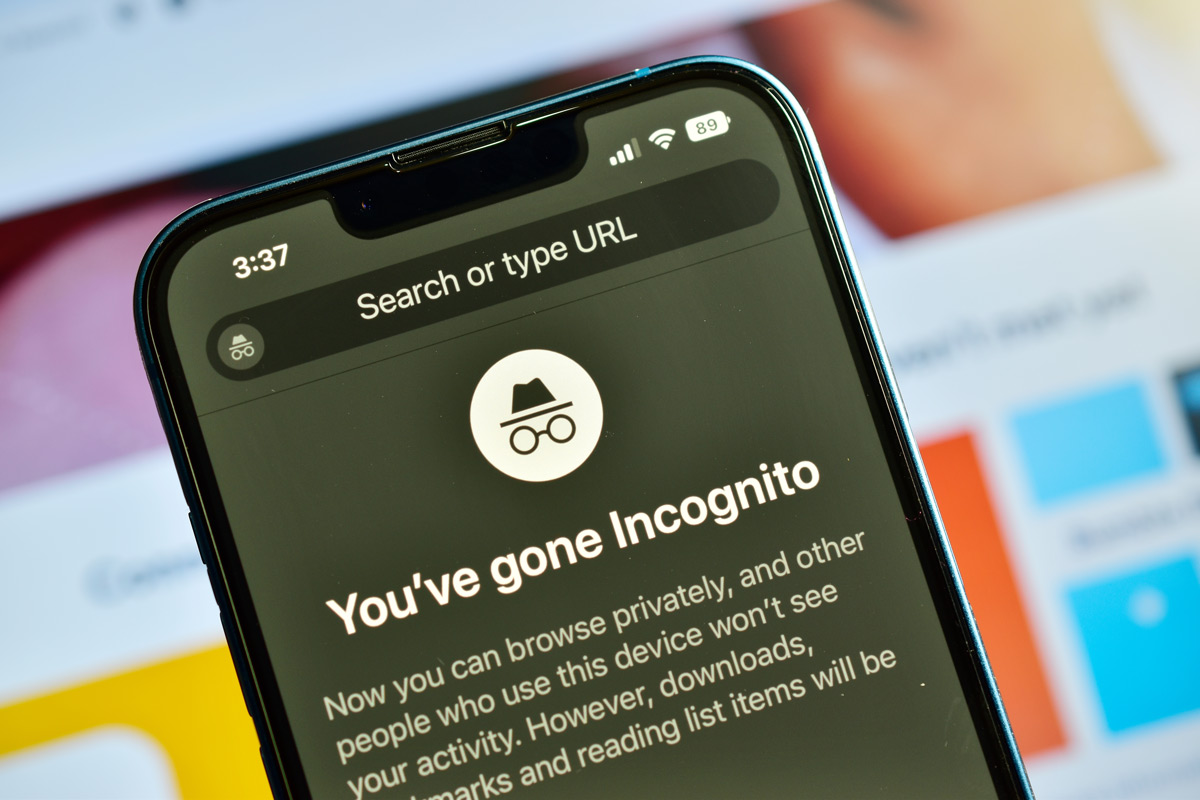
Google has agreed to delete billions of data records as a resolution to a lawsuit alleging the company improperly tracked the web-browsing activities

AT&T confirmed that data belonging to around 73 million present and past customers has surfaced on the dark web following a data breach.

Cybersecurity experts are issuing alerts to property holders throughout Tarrant County, Texas. Following a ransomware attack on the Tarrant Appraisal District (TAD). Experts advise immediate

A year ago, there seemed to be a glimmer of optimism in the ongoing battle of the cybersecurity industry against ransomware groups. It